 232
232
Many RCBC employees will utilize our enterprise applications such as Colleague or Informer in their daily responsibilities. Access to these systems should be handled with the utmost care and confidentiality when accessing student or employee records. Confidential records and information should strictly be accessed for job related duties and should not be shared or discussed in any way with non-authorized parties. Violations of this policy may be subject to disciplinary action.
This policy applies to all college employees including but not limited to: student workers, part-time staff, full-time staff, temp employees, interns, etc. If you are employed in any manner by Rowan College at Burlington County, then this pertains to you. Please review the following information.
Information Zone
 Cybersecurity is defined as the practice of defending computers, servers, mobile devices, electronic systems, networks and data from malicious attacks. Cybersecurity is considered a shared responsibility throughout the entire college community. OIT invests a tremendous amount of time and resources into technical tools and practices to protect our IT infrastructure, however, the most important weapon in our arsenal is ensuring all RCBC employees are prepared to identify and act on potential threats and areas of vulnerability when necessary.
Cybersecurity is defined as the practice of defending computers, servers, mobile devices, electronic systems, networks and data from malicious attacks. Cybersecurity is considered a shared responsibility throughout the entire college community. OIT invests a tremendous amount of time and resources into technical tools and practices to protect our IT infrastructure, however, the most important weapon in our arsenal is ensuring all RCBC employees are prepared to identify and act on potential threats and areas of vulnerability when necessary.
It is vital to understand that every RCBC employee is a critical component of RCBC’s best defense to the relentless cyber-attacks that occur almost every minute of every day
Did You Know?
- Attackers may study a victim’s Facebook, LinkedIn account and any other social networking accounts to gain intelligence about a victim and choose the names of trusted people in their circle to impersonate or a topic of interest to lure the victim and gain their trust.
- An estimated 91% of hacking attacks begin with a phishing or spear-phishing email.
- Although firewalls and other security products on the perimeter of a company’s network may help prevent other types of malicious traffic from entering the network—for example through vulnerable ports—email is generally considered legitimate and trusted traffic and is therefore allowed into the network.
- Email filtering systems can catch some phishing attempts, but they do not catch all of them.
- Phishing attacks are so successful because employees click on them at an alarming rate, even though the emails are obviously suspicious.
- Attackers will spoof the email addresses of your supervisors, coworkers, vendors, family, and friends in an attempt to fool you into thinking you have received a safe email from somebody you know.
What is phishing?
- Phishing refers to malicious emails that are designed to trick the recipient into clicking on a malicious attachment or visiting a malicious web site.
- Spear-phishing is a more targeted form of phishing that appears to come from a trusted acquaintance. Whereas ordinary phishing involves malicious emails sent to any random email account, spear-phishing emails are designed to appear to come (i.e., via spoofed email addresses) from someone the recipient knows and trusts—such as a supervisor, colleague, business manager or human resources department—and can include a subject line or content that is specifically tailored to the victim’s known interests or industry.
In the News:
Just recently, a number of faculty and staff at another NJ County College received a phishing email appearing to come from the Interim President, who did not send the email. The subject of the email was ““[ATTENTION REQUIRED] Revised Business Development, Implementation, and Review of Guidelines and Goals”. Staff who opened the email file attachment have since been subject to identify theft.
Tips to Stay Safe When Handling Spam
- When you receive a message you believe to be spam or from other malicious origins - Select the message in your Inbox and report it as “Spam” as shown in the screenshot below:
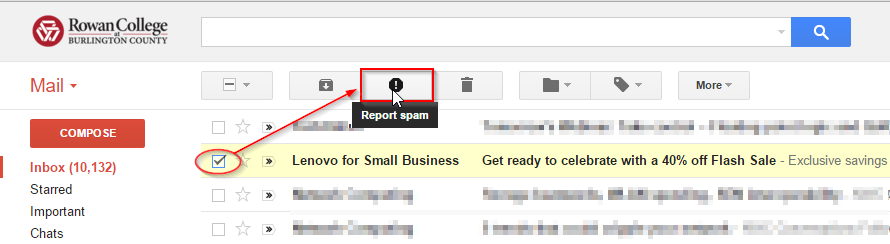
- Please remember to check your local “Spam” folder (label) on a regular basis to check for legitimate emails and purge accumulated spam as shown in the screenshot below:
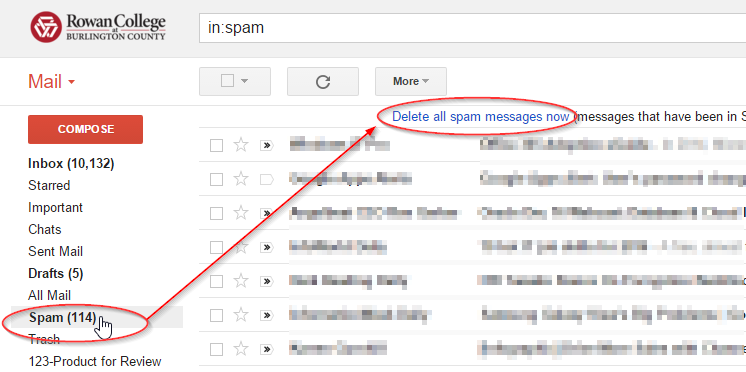
-
Remember
- NEVER share your account credentials with anyone or auto save login credentials. OIT will never ask you for your password to assist in recovering access to your account.
- NEVER save your account passwords on public or shared computers.
- You will NEVER be prompted for personal information (e.g., SSN and DOB) via an email or text message request from RCBC or any legitimate organization.
- NEVER send Personal Identifiable Information (PII) or sensitive financial data via email, instead copy the file to a shared network drive.
- ALWAYS verify requests for data verbally, even if it appears to be requested in an email from your supervisor, a member of senior staff or colleague – email addresses can be faked (spoofed). Don’t hesitate to pick up your phone and speak to the actual person that it appears sent you an email requesting data or information.
- DO NOT open, reply to, or click on links from suspicious emails that you receive.
- NEVER open/download attachments from emails you believe to be suspicious.
- Contact the RCBC OIT department if you suspect unusual activity with any of your RCBC accounts.
-
Thank you for reviewing this content. If you have any questions regarding any of the information on this page, then please contact your supervisor or the office of information technology.



